Verify Webhook Signatures
When setting up a webhook you can optionally add a secret, this will be used to sign all outgoing webhook requests. Any webhook with no secret will not be signed. The signature can be found in the event header as Podium-Signature.
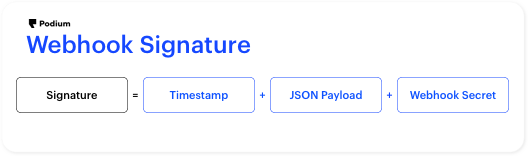
Values used to verify a webhook event from Podium
To verify the payload is from Podium, follow these steps:
Step 1: Extract the timestamp and signature from the header
- Get the timestamp from the header
podium-timestamp - Get the signature from the header
podium-signature
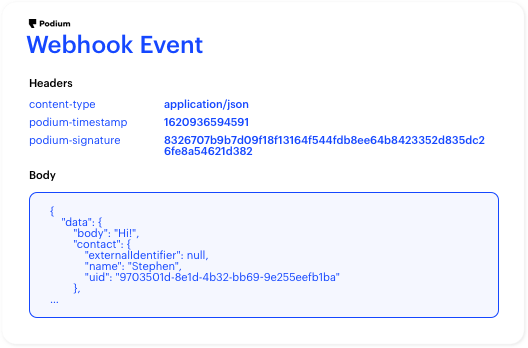
An example webhook event with the headers needed for signature validation
Step 2: Prepare the signed_payload string
The signed_payload string is created by linking the following items in order:
- The timestamp (as a string)
- For example:
1620771659663
- For example:
- The character
. - The actual JSON payload (i.e., the request body)
- For example:
{"data":{"bar":"apples","foo":"1"},"metadata":{"event_type":"test.event","version":"2021.04.01"}}
- For example:
Putting that all together would give us:
1620771659663.{"data":{"bar":"apples","foo":"1"},"metadata":{"event_type":"test.event","version":"2021.04.01"}}
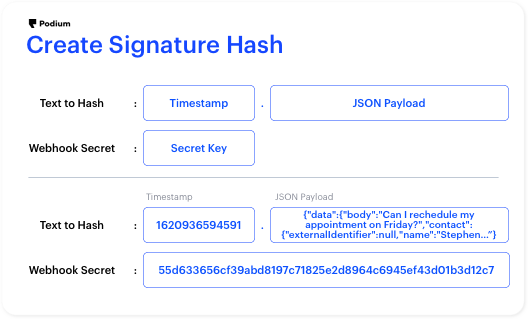
Create the webhook signature with the timestamp, JSON payload of webhook event, and webhook secret
Step 3: Determine the expected signature
Now we will hash the signed_payload string created in the previous step using the SHA256 hash function with the shared webhook_secret as the key.
Here is a website you can use to test the hashing functionality https://www.devglan.com/online-tools/hmac-sha256-online
Step 4: Compare the signatures
Compare the signature in the header to the expected signature. If the two signatures match, then you can safely assume that the payload is from Podium and has not been tampered with.
Updated over 4 years ago
